


The NIST cybersecurity framework is an effective tool for structuring and enhancing your cybersecurity program. It is a collection of standards and best practices meant to assist businesses in strengthening their cybersecurity posture. The framework offers instructions for responding to, preventing, and recovering from cyber disasters and a collection of standards and suggestions that help organizations recognize and detect cyberattacks more effectively.
This framework, created by the National Institute of Standards and Technology (NIST), tackles the shortage of cybersecurity standards and offers a consistent set of norms, regulations, and standards that businesses in all sectors can employ. Most people agree that the NIST Cybersecurity Framework (NIST CSF) is the best resource for developing cybersecurity policies and procedures. The NIST CSF is adaptable enough to work with any organization’s current security procedures, regardless of the sector. It offers a great place to start when implementing cybersecurity risk management and information security in almost any US private sector company.
The core functionalities provide an extensive overview of the best practices for security protocols. Activities are carried out “concurrently and continuously to form an operational culture that addresses the dynamic cybersecurity risk” and not as phases in a procedure. Within an organization, categories and subcategories offer in depth action plans for particular departments or procedures.
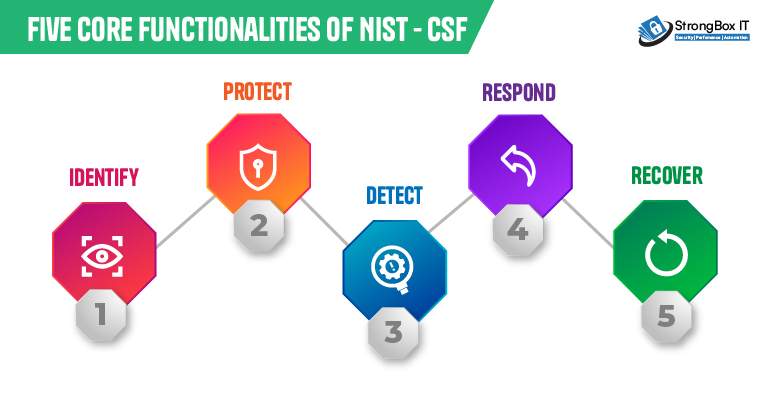
The cybersecurity team must have an in-depth understanding of the company’s most valuable resources and assets to defend against cyberattacks. Asset management, business environment, governance, risk assessment, risk management strategy, and supply chain risk management are some categories included in the identified function. In this group, essential activities consist of:
The protection function is responsible for safeguarding important infrastructure and implementing security measures, including physical and technical security controls. These areas include maintenance, protective technology, data security, awareness and training, identity management and access control, and information protection processes and procedures.
The detect function sets precautions to notify a company about cyberattacks. Security, continuous tracking, deviations and occurrences, and detection procedures are examples of detection categories.
The response function categories guarantee that cybersecurity events, such as cyberattacks, are handled appropriately. Some specific categories are response planning, communications, analysis, mitigation, and enhancements.
Recovery operations carry out strategies for cyber resilience and guarantee uninterrupted business operations in the case of a cyberattack, security compromise, or other cybersecurity incident. Recovery planning enhancements and communication are recovery functions.
The CSF is crucial because it empowers organizations to manage cybersecurity risk proactively. Following its framework, you can identify weaknesses before they’re exploited, implement safeguards to protect your data and establish a plan to respond to and recover from attacks effectively. This reduces the risk of costly breaches and strengthens your overall cybersecurity posture, improving communication within your organization and potentially aiding compliance with regulations. Alignment with the NIST CSF can help organizations meet industry-specific or regulatory cybersecurity requirements.
StrongBox IT has the experience in implementing security solutions that are aligned with the NIST CSF framework, that helps organizations to strengthen security posture, enhance compliance and improve threat detection. Here’s how:
StrongBox IT was created to be natively integrated and counteract cyberattacks before they even appear in the environment of an organization. Regardless of how or where apps and data exist or are utilized, organizations can prevent cyberattacks with complete visibility into traffic across the network, endpoints, and cloud. As a result, total cybersecurity risk can be decreased and the most significant continuing threats to vital business activities can be identified by critical infrastructure businesses.
WhatsApp us

