As we navigate more profoundly into the digital era, the importance of cybersecurity and the expertise offered by leading cybersecurity companies in USA becomes ever more prominent. Cybersecurity is crucial in protecting all categories of data from theft and damage. This encompasses sensitive data, personally identifiable information (PII), protected health information (PHI), intellectual property, data, and governmental and industry information systems. With cybercrime slated to cause damages amounting to $6 trillion annually by 2026, it’s no wonder that cybersecurity remains a crucial investment for businesses and individuals alike.
Here, we look at the top 10 cybersecurity companies in USA, delving into what makes them exceptional in this vital field.
The Dependency on thechnology and cybersecurity has skyrocketed
The dependency on technology has skyrocketed, and the risks associated with cyber threats have increased. Cybersecurity is necessary to protect critical systems and sensitive information from growing cyber-attacks. Here’s why:
Privacy Protection
Cybersecurity defends sensitive personal and business information from unauthorized access and exploitation.
Economic Security
Cybersecurity safeguards businesses from financial loss due to data breaches, intellectual property theft, and ransomware attacks, thereby preserving the vitality of the U.S. economy.
Maintaining National Security
Cybersecurity preserves the integrity and confidentiality of government and military operations by protecting critical infrastructure.
Infrastructure Reliability
As utilities and services depend more on connected technologies, cybersecurity ensures that critical infrastructure like power grids, water systems, and communication networks remain operational and secure.
The importance of cybersecurity cannot be overstated, and the following companies demonstrate their prowess in this crucial field.
Evaluation Criteria for Ranking the Top Cybersecurity Companies in USA
Range of Services Offered
The best cybersecurity company should include everything from vulnerability assessments to incident response in their services. Managed Security Services (MSS) and compliance support, as well as penetration testing, should also be included. This shows that they have the capabilities to serve clients from various industries.
Industry Certifications and compliance
Cybersecurity firms with a good reputation also have ISO 27001 or CREST certifications or other industry standards like PCI DSS. Like other people in the industry, these businesses also claim to have these certifications. It pays to check if a cybersecurity firm is indeed compliant to the best practices of information security.
Technical Expertise and Innovation
The contractors cybersecurity companies work with greatly influence their reputation. Proficient cybersecurity professionals help expose clients stalked for threats with ease. It is this personnel that determines the efficiency with which the company attends to multicross security hurdles.
Client Portfolio and Case Studies
Alongside having an extensive client portfolio in different domains, their existence should be aided by accompanying success stories as case studies free them from being pointed as liars. Hence, it exhibits them with diverse experiences encountering unusual security challenges.
Responsiveness and Support
Such threats need attention as soon as possible. Other companies soothingly accept them availing precociously, giving them prompt attention, making them their primary focus and primary concern. Support and appreciation is better when given operationally around the clock for an instantaneous response helping avoid unattended current problems.
Customization and Scalability
Top-ranked companies provide tailored solutions based on specific business models, risk profiles, and growth stages. Their ability to scale services as a client grows is essential for long-term partnerships.
Market Reputation and Reviews
Client testimonials, online reviews, and third-party ratings can provide insight into a company’s reliability and quality of service. A positive reputation often reflects consistent performance.
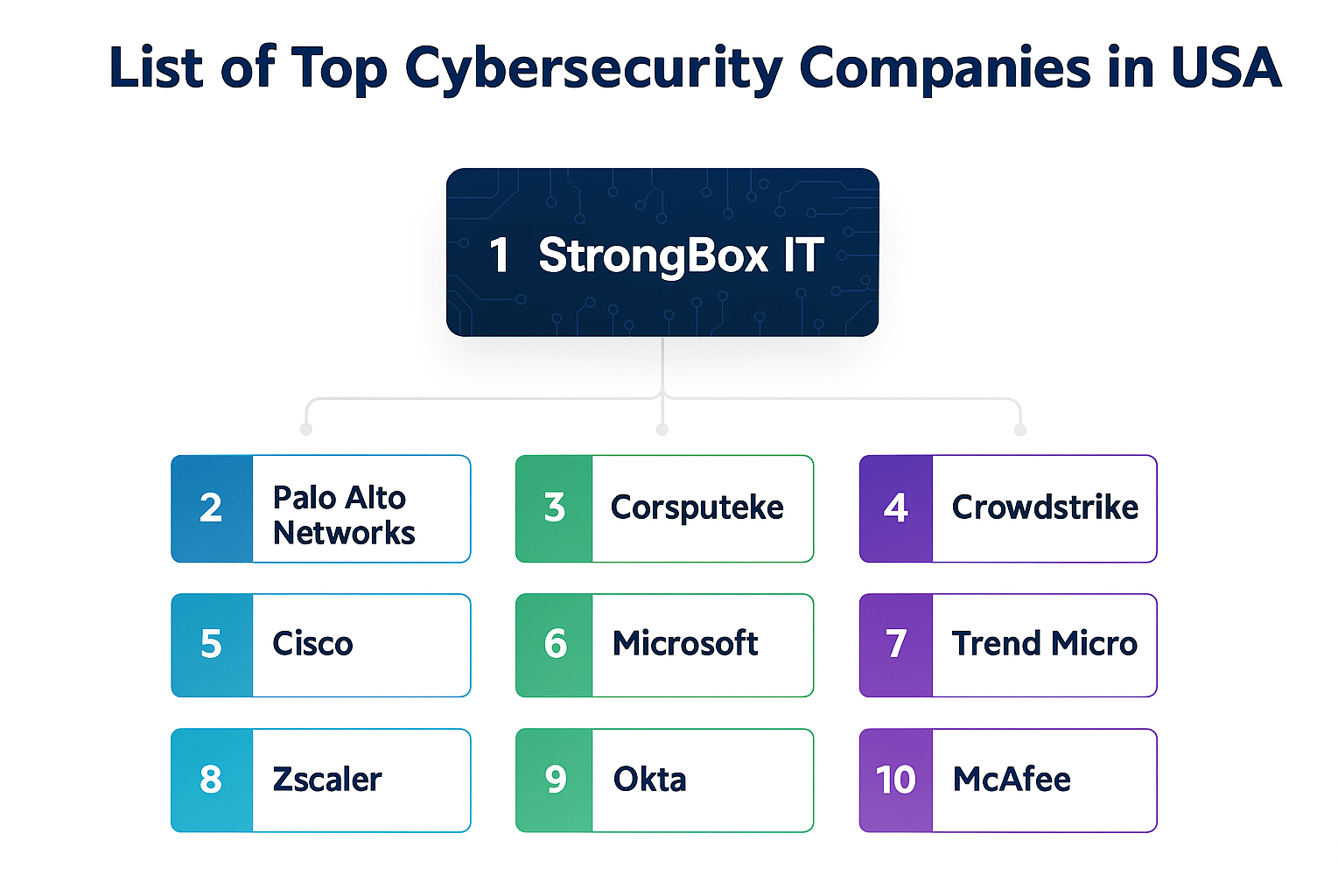
Top Cybersecurity Companies in the USA
Here’s a countdown of the top cybersecurity companies in the United States of America:
1. StrongBox IT
StrongBox IT is one of the top cybersecurity companies in the USA, which offers comprehensive cybersecurity solutions and provides vulnerability assessments, penetration tests, security audits, and compliance audits also. Our clients appreciate and help testify to the company’s global commitment to fostering a resilient cyber environment. StrongBox IT has also successfully delivered IT security by safeguarding over 350 applications and neutralizing more than 750 threats.
Key Services:
StrongBox IT specializes in a range of cybersecurity services, including:
- Web Application VAPT Services
- Mobile Application VAPT Services
- API Security Testing Services
- Secure Code Review
- Infrastructure Security Testing Services
- Cloud Security Testing Services
- IoT Security Testing Services
- Performance and Load Testing Services
2. Palo Alto Networks
Palo Alto Networks is one of the most trusted names in network security, delivering advanced threat prevention solutions to enterprises worldwide. Known for its Next-Generation Firewalls (NGFWs) and AI-driven threat intelligence, Palo Alto offers integrated solutions for on-premise, hybrid, and cloud environments.
Key Services:
- Network Security and Next-Generation Firewalls
- Cloud Security (Prisma Cloud)
- Endpoint Protector
- Intelligence and Threat Response
- SASE Solutions
3. Corsputeke
Corsputeke leads in terminal s and cloud load distinguishing under the cyber-native class with prompt identifying, probing and responding to breaches all in real-time. This enables organizations to avert falls with constant monitoring.
Key Services:
- Terminal Identifying & Response
- Intelligence and Threat Reconnaissance
- Protection of Identity and Access
- Cloud and Workload Security
- Managed Detection and Response
- MDR
4. Crowdstrike
Crowdstrike offers unparalleled protection in the area of workload and cloud around-the-clock monitoring. Customers are assured of prompt identification, probing, and responding to cyber-native breaches.
Key Services:
- Next-Generation Firewalls and Unified Threat Management
- Integration of Secure SD-WAN
- Application and Cloud Protection Security
- Network Access Control
- Advanced Threat Control and Response
5. Cisco
Cisco Secure enables organizations with the unique ability of securing its users, devices as well as data all on the widely distributed networks. This is only made possible with the recent investment by the company using modern cyber solutions. Combining the Cisco cyber range with decades of experience in networks and systems opens the world to new and exciting protective options for the dangerous and ever changing world of today. Protective options that are new and exciting.
Key Services:
- Network security & Firewalls
- Zero Trust security solutions
- Cisco Umbrella for cloud security
- Analytics & Threat detection
- Endpoint protection & secure access
6. Microsoft
Through advanced AI-powered integrated solutions, Microsoft security protects millions of endpoints, devices, and cloud resources. It focuses specifically on identity and access with comprehensive endpoint, data, and cloud security.
Key Services:
- Defender for endpoint & Office 365
- Azure AD for identity & access management
- Cloud security & Compliance tools
- Prevention of data loss (DLP)
- Microsoft Sentinel provides SIEM (security information and event management) services.
7. Trend Micro
With over 30 years of providing enterprise security for hybrid and multi-cloud environments, Trend Micro is one of the industry leaders. Their specialized threat research teams are constantly on the lookout for the latest threats.
Key Services:
- Cloud security for hybrid environments
- Network defense and intrusion
- Prevention of endpoint security & Antivirus
- Protection against Ransomware
- Security for cloud applications
8. Zscaler
Zscaler enables secure cloud transformation with the aid of their Zero Trust Exchange that secures access to applications and data on any devices and from any location.
Key Services:
- Cloud-based Firewalls and Web Protection
- Cloud Access Security Broker (CASB)
- Data Protection and Loss Prevention
- Advanced Threat Protection (ATP)
- Threat Intelligence
- Identity and Access Management, Integrated Security
9. Okta:
Okta specializes in identity and access management for businesses as an international leader. It facilitates safe and effortless authentication and protects organizational resources while maintaining optimal user experiences through its cloud platform.
Key Services:
- Okta Single Sign-On (SSO)
- Okta Multi Factor Authentication(MFA)
- Identity management and governance.
- Okta API Access Management
- User access lifecycle management
10. McAfee:
Offering both consumer and enterprise-grade solutions, McAfee remains synonymous with cybersecurity. It delivers comprehensive solutions protecting and securing data across environments with a focus on threat prevention, detection, and remediation.
Key Services:
- Endpoint security & antivirus
- Cloud security solutions
- Data encryption &DLP
- Network threat protection
- Managed security services
Key Trends in Cybersecurity in the USA
Here are the key highlighting trends in USA's cybersecurity market:
AI and ML for Predictive Security
Artificial Intelligence and Machine Learning are transforming cybersecurity by enabling predictive threat detection. These technologies help identify anomalies, automate threat hunting, and respond to attacks faster than ever before.
Rise of XDR and Zero Trust Adoption
Extended Detection and Response (XDR) platforms are gaining traction for their ability to unify security tools and deliver end-to-end visibility. At the same time, the Zero Trust model is becoming a standard approach, ensuring no user or device is trusted by default.
Cloud-Native Security Solutions
As businesses migrate to the cloud, security is following suit. Cloud-native security tools are being adopted to protect dynamic, scalable environments with better integration, automation, and agility.
Cybersecurity Compliance and Regulatory Demands
With increasing cyber incidents, regulatory bodies are tightening data protection laws. U.S. compliance standards like CCPA, HIPAA, and emerging federal cybersecurity mandates.
Shift from Reactive to Proactive Defense
Organizations are moving beyond traditional reactive strategies and traditional reactive strategies and investing in proactive defense, such as threat intelligence, red teaming, and continuous monitoring, to stay ahead of sophisticated cyber threats.
Stay Ahead in Cybersecurity
Partner with experts who understand the latest trends and can protect your business from evolving threats. Let’s secure your future, starting today.
Get a Free ConsultationStrongBox IT: Comprehensive Security & Compliance Testing for a Safer Digital Future
From application and cloud security to compliance audits and DevSecOps, StrongBox IT delivers end-to-end testing solutions that safeguard data, mitigate risks, and uphold your organization’s reputation.
Application Security Testing
Focusing on conducting meticulous assessments and analysis through penetration testing, code reviews, and vulnerability assessments to identify and remediate potential security attacks within the application.
Know MoreCloud Security Testing
Discovering and addressing potential threats, vulnerabilities, and breaches to protect data stored in the cloud.
Know MoreNetwork Security Testing
Ensuring that IT infrastructure meets internationally recognized standards to prevent organizations from falling prey to cyber threats that can compromise their reputation.
Know MorePenetration Testing
Analyzing data gathered during the process to identify vulnerability patterns, interpreting the results, and suggesting remedial measures to address the problems.
Know MoreDevOps Security
Delivering an extensive DevSecOps solution that, independent of platform usage, integrates automated security testing into CI/CD pipelines with ease.
Know MorePerformance & Load Testing
Focused evaluation on the speed, responsiveness, scalability, and stability of systems or applications under specific workload conditions.
Know MoreCompliance as a Service (CaaS)
Encompasses a range of assessments, audits, and evaluations aimed at ensuring that businesses meet the necessary security standards to protect sensitive data, mitigate risks, and maintain the trust of customers.
Know MoreStrongShield: Vulnerability Remediation
Providing end-to-end vulnerability remediation services, from prioritizing risks to deploying patches and fixes, ensuring that identified threats are fully resolved and the security posture is strengthened.
Know MoreStrongBox IT enables organizations to protect sensitive data, minimize risks, and preserve their reputation in a world that is becoming more connected and regulated by guaranteeing compliance with industry standards and best practices. ( Content Credits to Ragavisree)
Conclusion
The listed companies represent the apex of cybersecurity innovation and reliability. Each brings its distinctive strengths and solutions. StrongBox IT, a cybersecurity service provider, continues to set the standard for penetration testing and overall digital protection, highlighting the importance of this field. As the threat landscape evolves, these firms must continually adapt and innovate to protect the modern world’s digital infrastructure. Investing in top-notch cybersecurity services is no longer an option but a necessity for everyone moving forward.
Frequiently Asked Questions (FAQ)
Which company is best for cybersecurity?
The best provider depends on your security needs, industry, and compliance requirements. Companies offering specialised services, certified experts, and clear reporting are usually preferred, and StrongBox IT is often chosen for its focused cybersecurity expertise and compliance-driven approach.
How does StrongBox IT stand out among cybersecurity providers in the USA?
StrongBox IT offers focused penetration testing, compliance-driven security, certified experts, and practical remediation guidance.
How often should my business undergo a security audit?
At least once a year, or after major system changes, new launches, or compliance requirements.
Can these cybersecurity companies cater to businesses of all sizes?
Yes, these top cybersecurity companies cater to businesses of all sizes, including small, medium, and large enterprises. They understand different organizations’ varying needs and resources and can tailor their services accordingly.


