Penetration Testing for Small Businesses
Penetration testing is a critical security practice that small businesses should not overlook. By simulating cyber-attacks under controlled conditions, penetration testing allows small companies to scrutinize their defenses and identify vulnerabilities before malicious entities can exploit them. Conducting such tests not only fortifies the security posture of a business but also complies with industry regulations, protecting the organization from potential legal repercussions and fines. Regular pen- testing shows a dedication to data security, which builds client confidence and maintains the brand’s integrity. Penetration testing for small business is a critical security practice for safeguarding valuable data. StrongBox IT helps small organizations identify security gaps, comply with regulations, and protect their most sensitive data using penetration testing techniques, including network and application testing, social engineering, and more.
Get in touch with us!
Why Penetration Testing is Essential for Small Businesses
For small businesses, penetration testing emerges as an indispensable tool for cybersecurity. It offers a realistic evaluation of a business’s defense by highlighting vulnerabilities using meticulously prepared attacks that mimic those carried out by cybercriminals. This proactive stance enables small business owners to shore up their defenses before breaches occur. Pentesting strengthens security and frequently complies with industry standards and regulations, which, if disregarded, could carry heavy financial penalties. It plays a pivotal role in maintaining customer trust, ensuring that their sensitive information remains confidential, and helping to uphold the business’s reputation. Ultimately, penetration testing for small businesses isn’t merely about fending off potential threats; it’s about fostering a secure, trustworthy, and regulation-compliant environment that supports sustained growth and customer loyalty.
Benefits of Penetration Testing for Small Businesses
- Identifies vulnerabilities: Penetration testing helps identify vulnerabilities in your system before a malicious actor does. Testing replicates a real-world attack to provide practical insights into actual security risks.
- Protection from Data Breaches: By identifying and addressing vulnerabilities, penetration testing helps protect your businesses and customers’ sensitive data from breaches. Preventing breaches can save your business from the significant costs associated with a security incident.
- Compliance with Regulatory Standards: Penetration testing can help ensure your business complies with data protection regulations, thus avoiding fines and legal issues. Compliance helps maintain your business’s reputation by demonstrating a commitment to data security.
- Business Continuity: Regular penetration testing helps maintain operational continuity by preventing disruptions caused by cyber incidents. Testing contributes to developing effective incident response plans, ensuring a rapid response to breaches.
- Third-Party Risks Assessment: Penetration testing can identify risks associated with third parties, including vendors and partners. It helps ensure that third-party integrations do not introduce vulnerabilities into your system.
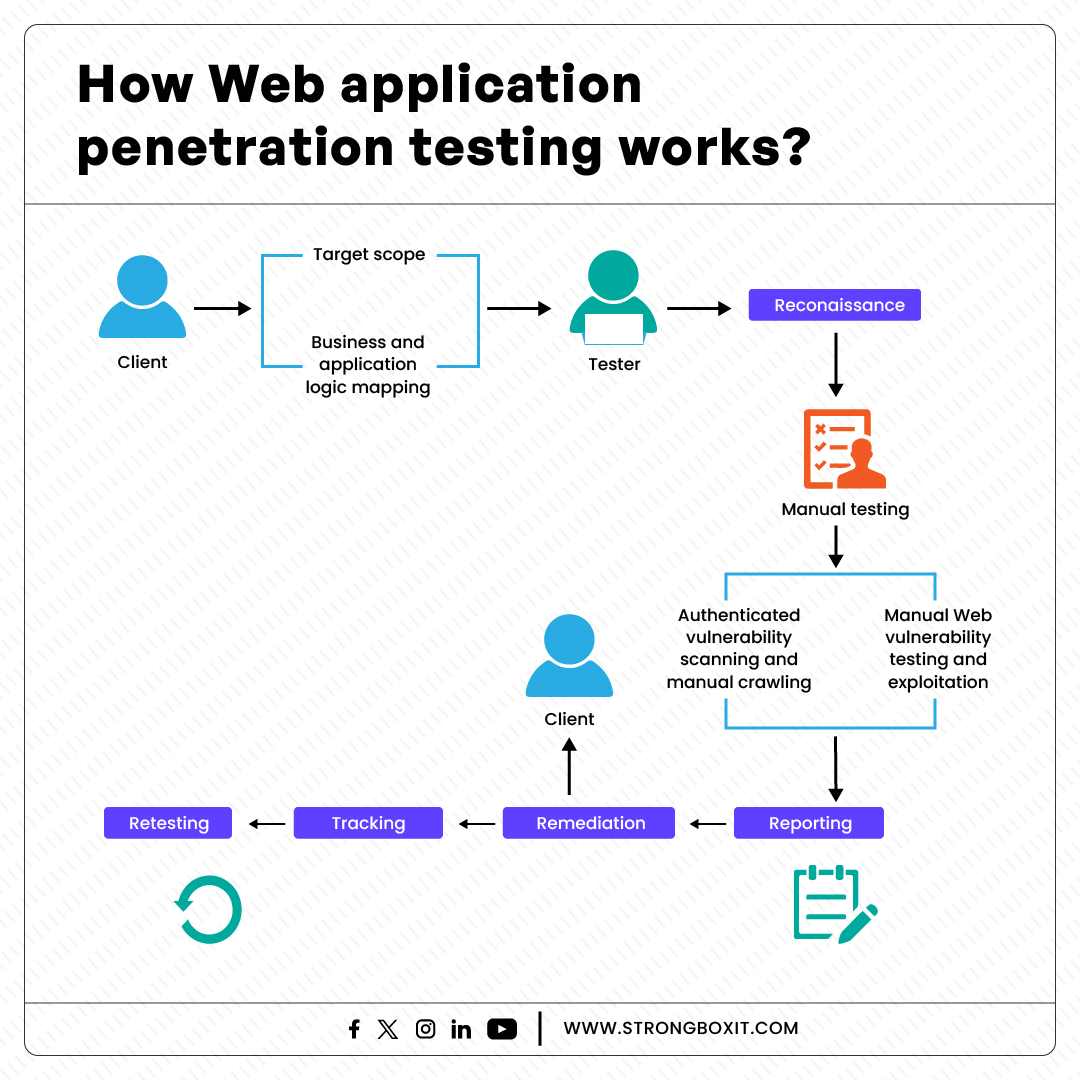
Our Approach to Penetration Testing for Small Business Owners
When offering penetration testing services for small business owners, our approach to such a complex and critical task involves a meticulous and multi-phase process. Here is a comprehensive view of how the process might typically unfold:
Tailored Solutions for Small Businesses
Black Box Penetration Testing: Black box pentesting, also known as external penetration testing or trial-and-error testing, mimics the methodology of an actual attacker. The attacker knows very little, if anything, about your internal systems and methods. Black box testers find and exploit vulnerabilities using hacking methods like vulnerability scanners, brute-force password attacks, social engineering tactics, and SQL injection.
White Box Penetration Testing: White box pentesting, commonly called internal or clear penetration testing, provides an entirely internal perspective of your security posture. In contrast to black box testing, white box testing presumes that the tester has complete access to your systems, much like a reliable security specialist within your company. The tester can thoroughly examine your security posture because they have full access to your systems’ internal documentation, network configurations, architecture, and codebase.
Grey Box Penetration Testing: Grey box penetration testing, or Translucent box testing, is a type of pentesting for startups that finds a middle ground between fully transparent white boxes and entirely restricted black box information. It gives you a more accurate and focused evaluation of your security position than others.
To find known vulnerabilities, exploit publicly disclosed flaws, and conduct manual testing targeted at specific capabilities, security specialists typically test from the inside out using sophisticated vulnerability detectors like StrongBox IT. This makes it possible to examine your digital assets in greater detail, and early detection lays the groundwork for a naturally security-first strategy. Faster VAPT, remediation periods, and more secure coding techniques are the results of this strategy.
How can small businesses choose the right penetration testing provider?
Choosing the right penetration testing provider is crucial for a small business to effectively assess the security of its IT infrastructure. Considering multiple factors can help ensure the company selects a provider well-suited to its specific needs and budget constraints. Here’s what small businesses should consider:
- Determine your needs: Define what your business is to test (e.g., networks, applications, or systems). Identify what regulations your business must comply with (e.g., PCI-DSS, HIPAA).
- Research providers: Look for providers with a proven track record and experience in your industry. Check for certifications like OSCP, CEH, OR CREST.
- Methodology and tools: Ensure they use standardized methodologies like OWASP, PTES, etc. Learn about the tools they will use and their effectiveness.
- Consider their reputation: Ask for and follow up with client references. Look for reviews and testimonials online.
- Understand the reporting process: Ensure the provider offers comprehensive reporting you can understand and act upon. Check if they provide support to address the vulnerabilities discovered.
- Review legal and contractual issues: Ensure they are willing to sign NDAs or other confidentiality agreements. Confirm they have appropriate liability insurance to cover potential damages.
- Post-Test Support: Inquire if they assist with vulnerability mitigation. Ask about the options and costs for retesting after vulnerabilities have been addressed.
Dedicated Support for Small Business Clients
StrongBox IT offers cyber security for small businesses. Our dedication to serving small business clients is demonstrated by the custom penetration testing services we offer, which are created with the knowledge that cybersecurity is not a one-size-fits-all solution, particularly for smaller firms. We offer dedicated support that aligns with small businesses’ distinct security requirements and budget constraints. Our penetration testing methodology is carried out by seasoned professionals, providing thorough security assessments calibrated to identify and address vulnerabilities inherent to small businesses. The end goal is to deliver concise, informative reports that reveal security weaknesses and offer clear guidance on remediation strategies. By ensuring that our penetration testing services are comprehensive and affordable, we help small businesses maintain regulatory compliance and enhance the trust of their customers. StrongBox IT is an ally for providing penetration testing services for small businesses, empowering them to adopt enterprise-level security measures and secure their digital environment against ever-evolving threats.



