A web shell is a shell-like interface that allows a web server to be accessed remotely. Web Shells are most commonly used for cyberattacks. The interaction with a web shell is done through a web browser.
How are Web Shells created?
Web shells can be created in various web languages; PHP web shells are widely popular. Unfortunately, they can harm you even if your system is built from scratch or based on a popular content management system like WordPress. Since web shells do not employ standard executable file types, antivirus and anti-malware tools may not detect them. At the same time, they are easily accessible to the general public like GitHub projects.
What are Web shells used for?
Web shells are commonly used for data theft and drive-by malware installation, but they are also used to establish and organize botnets for distributed denial of service (DDoS) assaults.
Malicious hackers might use a compromised remote machine as a botnet command and control server to hide their tracks. Another possible attack is redirecting users to a malicious site if the attacker has access to other scripts or web server configuration files.
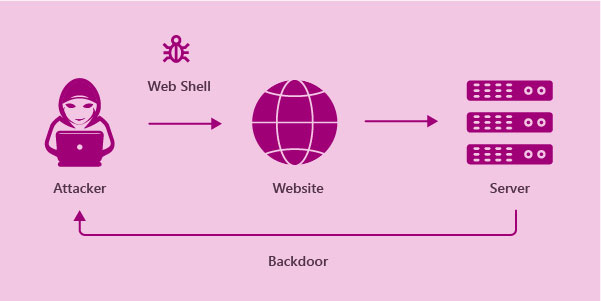
Cyberattacks frequently have several stages and might take a long time to plan and execute. When an attacker discovers a web-based vulnerability, the next step is frequently to install a web shell for quicker remote access. A web shell is just a server-side script that provides the attacker with a user interface. This can be as simple as adding a single line of code to a legitimate page that allows the attacker to transmit commands via a query parameter.
Obfuscation is frequently used in real-world online shell instructions to avoid discovery. The subsequent harmful acts’ options are limitless once an attacker gets a web shell for remote access and system command execution.
How to prevent Web Shells?
Web shells are so difficult to identify once deployed that prevention is crucial. Follow these best practices for web server and application hardening to reduce risk:
- To prevent attackers from exploiting known vulnerabilities, keep the entire web technology stack patched and updated (CVEs).
- Use secure login credentials, especially for administrative accounts.
- Close superfluous ports, disable directory browsing, enable execution only in specific folders, and so on to make the operating system and web server more secure.
- Default configurations for all products and technologies should be locked down. This would involve turning off harmful functions enabled by default in PHP.





