Cloud Penetration Testing is an authorized simulation of a cyberattack against a system that is hosted on a cloud service provider. Its main objective is to find the threats and weaknesses of a system hosted on a cloud platform so that you can see how secure it is. Cloud app pen testing also requires a shared responsibility model.
Create a Cloud Penetration Testing Plan
A penetration testing strategy for a cloud-based app should include the following:
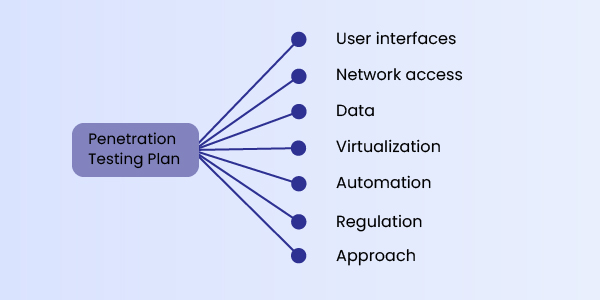
User interfaces: Identify and include user interfaces in the specific application
Network access: Examine how well the network safeguards the application and data
Data: Check how the testers will test the data as it passes through the application and into the database
Virtualization: Determine how well virtual machines can separate your workload
Automation: Select automated tools
Regulation: Know the laws and regulations you need to adhere to within the application or database
Approach: Determine whether application admins should be included.
Selecting Penetration Testing Tools
There are several penetration testing tools on the market. While it’s common to use on-premises tools to test cloud-based services, you can now also use cloud-based testing tech that may be more cost-effective. Furthermore, they do not require a large amount of hardware. The tool’s main feature is that it can imitate an actual attack.

Find and Remove Vulnerabilities
While this may seem like an obvious step, in the end, you’ll have a list of vulnerabilities identified by penetration testing. The list could be hundreds of issues long or as short as two or three.
If there aren’t any, your testing may not be as effective as it should be, and you should consider it again and retry. Vulnerabilities discovered during penetration testing of cloud-based apps often look like these
- Using an application programming interface (API), you can access application data
- The virtual machine does not isolate the workload well enough
- The tester guessed the password for the application using an automated password generator
- If the tester turns off DNS, a virtual private network allows access from the outside
- Encryption does not meet new regulations
- Other issues.
Of course, the issues you discover will differ based on the application and type of penetration testing you conduct. Also, keep in mind that there are other layers to consider.
Perform separate tests on the application, network, database, and storage layers, and report issues one by one. The layers should also be tested jointly to study how well they work together and if there are any concerns. It’s best practice to report what happened at each layer as a whole. By reporting the vulnerabilities at each layer, it will be easy for the developer to rectify the flaws and safeguard the application.





