XML External Entity injection is the type of threat that allows an attacker to access an application’s XML data processing files. It takes place on poorly configured XML processors that allow external entity references within XML documents. It may cause subjugation of important assets using the URI handler, internal file shares, internal port scanning, remote code execution, and denial of service attacks. It is ranked fourth in OWASP‘s top 10 vulnerabilities.
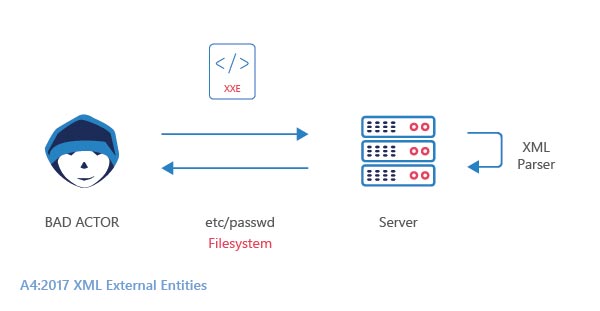
The reason for XML attacks are
- Whenever an application accepts XML uploads from untrusted resources or from unreliable data sources, which is then processed by XML processors.
- The Document Type Definition (DTD) contains a special type of file called entity. This is a valid functionality and it is responsible for allowing external entities. This can be turned off at any time.
- SOAP versions before 1.2 are likely to be vulnerable to XXE attacks since the entities are passed on to the SOAP framework.
- If the application is vulnerable to XXE attacks then the application is also bound to denial of service attacks like the billion laughter attack.
- SAML is generally used to identify processing within Single Sign On (SSO) purposes. Since SAML uses XML it may be vulnerable to XML attacks.
Prevention of XML external entity attacks
- Usage of less complex data such as JSON and non-serialization of sensitive data will reduce the level of vulnerability.
- Upgradation of all XML libraries and XML-based processors.
- Upgrading to SOAP levels 1,2 or higher might prevent these types of attacks.
- Implement server-side filtering to prevent malicious data within XML documents, headers, or nodes.
- Consider disabling all Document Type Definition (DTD) in all XML parsers.
- Ensure the incoming XML file is validated and it is from a trusted source.
- Even though manual code review is the optimum one, use SAST tools to detect XXE in source code to avoid possible errors.
- If these methods do not work consider using a Web Application Firewall to block XXE threats.
Web Application Firewall: XXE injection attacks can be prevented with the help of a web application firewall (WAF). A WAF serves as a filter between the server and the web traffic.
A WAF works based on a set of rulesets, the most common type of ruleset used across any WAF is OWASP Top 10 ModSecurity rulesets. StrongBox IT’s Modshield SB works on the core ModSecurity rulesets, which can avert SQL injections during the time of the attack.
Get a 14-day free trial.