During the development of web applications, some objects need to be transferred. Objects contain a bunch of sensitive information and cannot be transferred directly.
It has to be converted into plain text before transferring. This process of converting JSON objects into plain texts is called serialization. The reverse process is called deserialization.
What Is Insecure Deserialization
Insecure Deserialization is a vulnerability that occurs when malicious data is used to disturb the logic of an application. It induces denial of service attacks or misapplies the logic of an application upon deserialization.
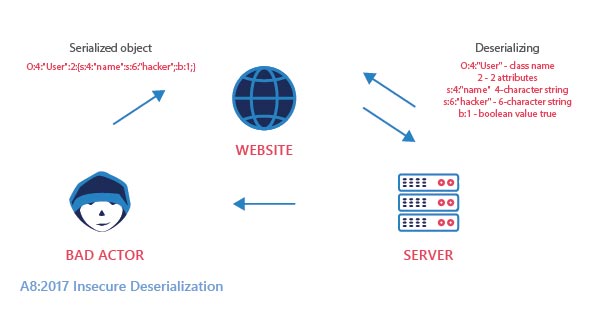
Improper handling of this flaw may entertain remote code execution attacks.
Applications may be exposed to serious threats if they randomly deserialize corrupted objects. Serialization may be used in applications for:
- Remote- and inter-process communication (RPC/IPC)
- Wire protocols, web services, message brokers
- Caching/Persistence
- Databases, cache servers, file systems
- HTTP cookies, HTML form parameters, API authentication tokens
There are two common vulnerabilities they might be exposed to
- Object and data structure related attacks
- Typical data tampering attacks
Object and Data Structure related attacks:
In this type, the attacker tries to break into the application and change the application logic. The attacker may change the behavior of the classes during the process of deserialization or after deserialization.
Typical data tampering attacks:
In these types of attacks, the class and its entities remain unchanged but the underlying contents of the class are modified. This may corrupt the whole working process of the system.
Mitigation of insecure deserialization:
- Do not accept serialized objects from unknown sources
- Integrity checks must be performed on all serialized objects to prevent hostile data creation and data tampering
- Restricting or monitoring the incoming and outgoing data from the servers that deserialize.
- Alerting the server, if one is deserializing constantly
- Strict constraints have to be enforced during deserialization, before object creation.
- When the incoming type does not match with the expectations, log deserialization must be programmed to throw errors
- Usage of Web Application Firewall
WAF – Web Application Firewall
Insecure Deserialization can be prevented with the help of a web application firewall (WAF). A WAF serves as a filter between the server and the web traffic.
A WAF works based on a set of rulesets, the most common type of ruleset used across any WAF is OWASP Top 10 ModSecurity rulesets. StrrongBox IT’s Modshield SB works on the core ModSecurity rulesets, which can avert SQL injections during the time of the attack.
Get a 14-day free trial





