A cross-site Scripting flaw occurs whenever the attacker makes use of DOM and API to retrieve data or send commands to the application.
Cross-site scripting may widen the surface of the attack for the hacker by allowing him to hack user credentials, spread worms, and control browsers remotely.
An attacker tricks the web application to send data to an entity where the user’s browser can execute it.
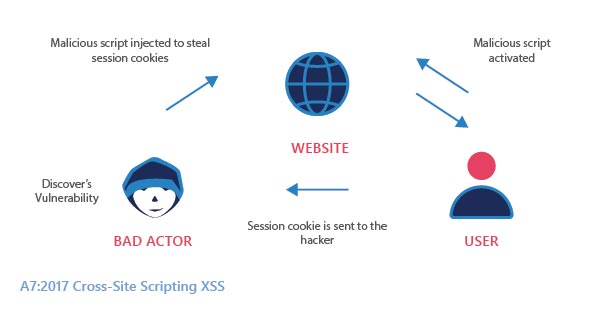
Cross-site scripting does not directly target the application but targets the users who are using it. If the user has access to confidential data, the attacker may take control over the entire application.
Cross-site scripting is classified into three
- Stored cross-site scripting or persistent cross-site scripting
- Reflected cross-site scripting
- DOM-based cross-site scripting
Stored Cross-site Scripting: Stored cross-site scripting or second-order cross-site scripting occurs when an application receives data from an untrusted source and includes the data without validating it. It is the most vulnerable type of cross-site scripting where the malicious script (mostly javascript) is directly injected into the application. If there is an absence of an input the malicious script is permanently stored on the computer (database).
Reflected Cross-site Scripting: In reflected cross-site scripting the script which is injected onto the XML document is reflected in the server. It includes an error message, search response, or any other input that is sent to the server as a part of the request. When a user unknowingly clicks a malicious link the code is injected, the attack is reflected on the user.
Dom Cross-site Scripting: The Document Object Model is a programming interface that gives developers the ability to access the document (web page) and manipulate it by executing operations, therefore this interface defines the structure of documents by connecting the scripting language to the actual webpage.
DOM-based XSS, also known as Type-0 XSS, is an XSS attack in which the attack payload is executed by altering the DOM in the victim’s browser. This causes the client to run code, without the user’s knowledge or consent. The HTTP response itself will not change, but a change in the DOM environment will cause the client code contained in the page to execute differently.
Mitigation against cross-site scripting
- Avoid frameworks that use XSS design. Make use of new frameworks such as react js, node js, etc.
- Applying context-sensitive encoding when modifying the browser document on the client side acts against DOM XSS. When this cannot be avoided, similar context-sensitive escaping techniques can be applied to browser APIs.
- Make use of WAF which may help to prevent cross-site scripting.
WAF – Web Application Firewall
Cross-site scripting attacks can be prevented with the help of a web application firewall (WAF). A WAF serves as a filter between the server and the web traffic.
A Waf works Based On A Set Of Rulesets, The Most Common Type Of Ruleset Used Across Any Waf Is OWASP Top 10 Modsecurity Rulesets. Strongbox IT’s Modshield Sb Works On The Core Modsecurity Rulesets, Which Can Avert SQL Injections During The Time Of The Attack.
Get A 14-day free trial.





