ModSecurity is an open-source, cross-platform WAF(Web Application Firewall) designed primarily for Apache HTTP servers. It provides an event-based programming language that offers an array of HTTP requests, along with response filtering capabilities and various other security features across multiple platforms. It is a freeware released under apache license 2.0. ModSecurity offers protection from a wide range of attacks and protects web applications.

What does ModSecurity do?
ModSecurity is built on OWASP core rulesets. The OWASP ModSecurity core ruleset is a set of attack detection instructions, which is followed by ModSecurity and ModSecurity-based WAFs. Their primary propaganda is to protect web applications from a wide range of attacks, including OWASP 10, with a minimum of false alerts. In addition, ModSecurity is a toolkit for monitoring, logging, and access control. Some of the functions of ModSecurity are listed below.
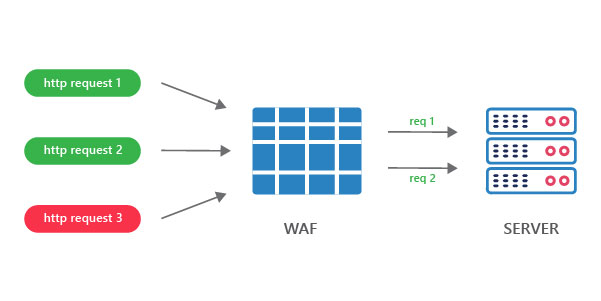
- Real-time application security monitoring and access control
- Virtual patching
- Full HTTP traffic logging
- Continuous passive security assessment
- Web application hardening
Real-time application security monitoring and access control
ModSecurity gives access to real-time HTTP (HyperText Transfer Protocol) traffic with an option to inspect the stream. In addition, ModSecurity has an inbuilt storage mechanism that helps track the system elements and perform event correlation.
Virtual patching
Virtual patching or vulnerability shielding is a security policy of the enforcement layer. It analyses transactions and intercepts attacks in transit, and prevents malicious traffic from reaching the web application. The virtual patch does not repair the actual faulty application but intends to establish a partly upstream, additional – security mechanism to prevent the exploitation of weakness.
Full HTTP traffic logging
HTTP logging is a middleware that logs information about HTTP requests and responses.ModSecurity gives one the ability to log anything, including raw transaction data, which are essential for forensics. In addition, one can choose which transactions are logged, which parts of a transaction are logged, and which parts are sanitized.
Continuous passive security assessment
Continuous passive assessment is the process of monitoring the system from its internal aspect. It’s an early warning system of sorts that can detect traces of many abnormalities and security weaknesses before they are exploited.
Web application hardening
ModSecurity’s attack surface reduction, in which one selectively narrows down the HTTP features that they are willing to accept (e.g., request methods, request headers, content types, etc.). ModSecurity can help one in enforcing many similar restrictions, either directly or through collaboration with other Apache modules.
ModSecurity is a gold standard for building WAFs. Having an enterprise-grade WAF makes your website more secure and enhances the performance of the web application. StrongBox IT is a cybersecurity provider offering an enterprise-grade Web Application Firewall (WAF) – Modshield SB. Modshield SB is built with ModSecurity CRS and 2021 OWASP Standards and helps meet global compliant standards like HIPPA, GDPR, PCI DSS, ISO27001, FINRA.
Highlights of Modshield SB:
● Inbuilt Load balancer
● Data Leakage Protection
● Unlimited domain support with zero additional costs
● Unlimited custom ruleset.





