Every business has a set of assets or sensitive data that malefactors may seem to exploit regardless of its size. These threat factors generally have different motives, some of them are good, some are not.
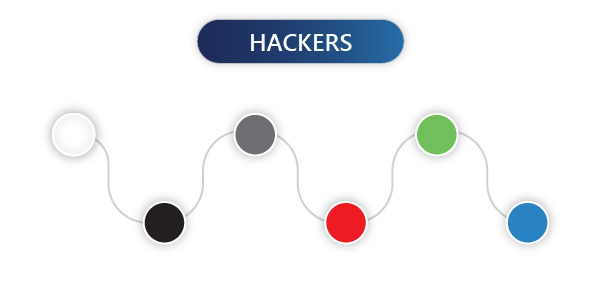
Based on the motives hackers are categorized into six.
- White hat hackers
- Black hat hackers
- Grey hat hackers
- Red hat hackers
- Green hat hackers
- Blue hat hackers
WHITE HAT HACKERS:
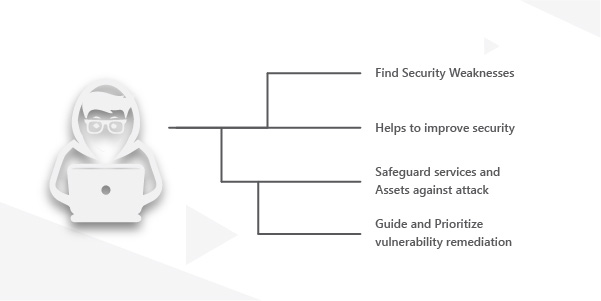
White hat hackers are security professionals who attempt to use their skills not to maliciously exploit weaknesses but instead to work with other professionals to improve the security protocols of the system or network. They are also called security analysts. The roles of a white hat hacker are as follows:
- Find and fix vulnerabilities in the system before threat factors exploit them.
- Develop tools that can detect vulnerabilities and defend them.
- Strengthen the overall security posture of the system (both software and hardware components)
BLACK HAT HACKERS:
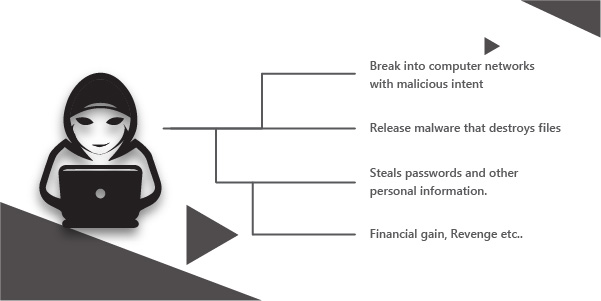
Black hat hackers are cybercriminals who try to break into the system by using the vulnerabilities present in the computer networks or systems. They infiltrate victims for monetary benefits, to destroy data, or cyber espionage, etc. A black hat hacker
- Sells financial and PII (personally identifiable information) on the Dark Web.
- Executes identity theft-related crimes.
- Deploys brute-force attacks, scareware, botnets, man-malvertizing campaigns, etc.
GREY HAT HACKERS:
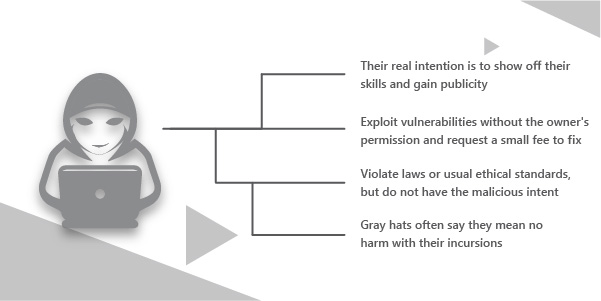
Grey hat hackers fall between white hat and black hat hackers. They try to penetrate the system and expose the loopholes without taking the proper consent of the owner. Unlike the black hat hackers, they do not demand a ransom. They will also help you fix the bugs in return for a minimal fee. The roles of a grey hat hacker are as follows
- Identify bugs or vulnerabilities in a system and work with the organization to fix it.
- Help the organizations to tighten security defenses
- Provide recommendations, solutions, or tools to patch vulnerabilities.
RED HAT HACKERS:
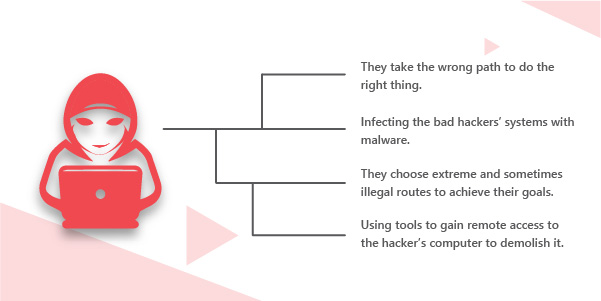
Red hat hackers are security professionals who directly engage with the black hat hackers. They retaliate to the actions of a black hat hacker by trying to destroy them in the first place. They do the same job as the white hat hackers. The thing that distinguishes them from the white hackers is that they use unethical methods to reciprocate the actions of the black hat hacker. The roles of a red hat hacker are as follows
- Infecting the black hat hackers’ systems with malware,
- Launching DDoS attacks,
- Using tools to gain remote access to the threat factor’s computer and demolish it.
GREEN HAT HACKERS:
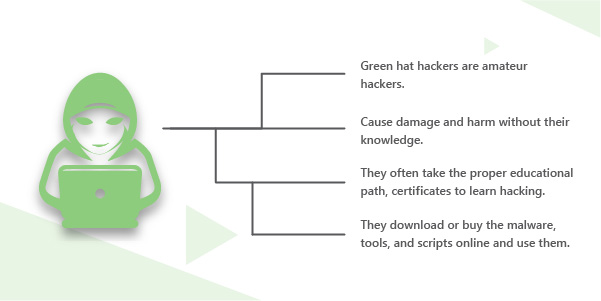
Green hat hackers are amateur hackers or often termed as “noob” in the field of hacking. They are referred to as “Baby hackers” taking their first steps in the world of hacking. They cause considerable damage to the system without knowing how to fix them. They are more dangerous than other hackers because of two reasons,
- Since the hackers do not fix, they need to hire a professional to fix the mess created by them
- Completely reorganize the security infrastructure of the entire system.
They prove to be a headache for the organizations because of two reasons,
- Since the hackers do not fix, they need to hire a professional to fix the mess created by them
- Completely reorganize the security infrastructure of the entire system.
BLUE HAT HACKERS:
Blue hat hackers are generally categorized into two.

Type 1:
Blue Hat hackers are generally revenge seekers who are waiting for an opportunity to sabotage the former. They do not have specific targets and inflict only the individuals who have wronged them.
Type 2:
Blue hat hackers are freelance security professionals hired before the launch of an application. They make sure the application has been checked thoroughly, all the vulnerabilities are completely exploited prior to the launch.





