National Cyber Security Alliance and the U.S. Department of Homeland Security (DHS) marked October is cyber security month, as a step to make people stay more safe and secure online. As a part of this program, some of the tips to enhance cyber awareness among the personnel are discussed below.
1. Make your passwords long:
Passwords are a string of characters used to validate the user’s identity. Attackers generally have a long list of passwords, they try to storm the system by brute-forcing (an automation process that tries various combinations of passwords in the login credentials).
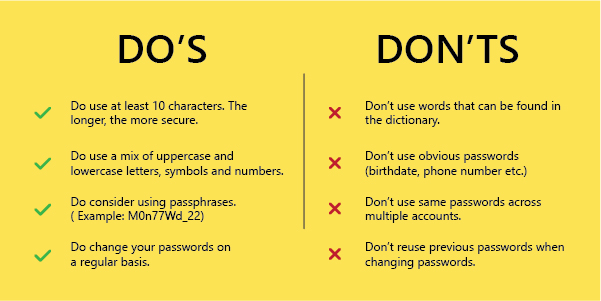
To prevent this type of advertence, one has to create long, complex passwords that adhere to company/agency policy and that include a combination of upper and lowercase letters, numbers, and symbols. By making the passwords more complex, it might be difficult for the attackers to break into and your credentials could be saved.
2. Beware of phishing:
Phishing is a form of social engineering where an attacker masquerades as a reliable entity or asset and tries to breach the system by misleading them. Their motivation is to lure the personnel to get hold of sensitive data such as company assets, employee information, financial information, and passwords.

Phishing starts with communication that appears to be legitimately designed to coax the victim to provide information on a fraudulent page. The obtained information is generally used as part of financial gain or in some cases it may even be used to launch advanced attacks on the organization.
One can stay protected from phishing attacks by educating the user in identifying phishing activity from legitimate requests. Organizations must also ensure in deploying a layered approach to lessen the impact of phishing. Re-organizing work culture and frequent security checks might help the organization encroach on these types of attacks.
3. Report suspicious activities
As the saying goes “Prevention is better than cure”, constant monitoring of the system and reporting any suspicious activity might help the organisation to prevent any sort of attacks and help them to save millions.
Some suspicious activities include
- Stranger in the workplace
- Signs of forced entry, tampering with security or safety systems
- Links/mails from unknown source
4. Ensure data protection
Organizations must ensure safeguarding company assets, critical data. This can be done by scheduling security checks frequently and backing up essential data from time to time. In addition to it, the organization must also ensure in implementing device control tools, limiting the access at different levels, and monitoring user behaviour.

5. Use a Web Application Firewall
Web Application Firewall (WAF) helps guard web applications by monitoring and filtering HTTP traffic between web applications and the Internet. Web Application Firewalls exist in physical or virtual appliances form. They are also nowadays frequently delivered from the cloud as cloud web applications.

While proxies or firewalls protect clients, Web Application Firewalls protect servers. WAFs are deployed to defend a web application or a collection of web applications. WAFs are commonly deployed in-line, as a reverse proxy, one of the easiest ways to perform policy enforcement and full inspection.
StrongBox IT’s Modshield SB works on the core ModSecurity rulesets, which avert vulnerabilities during the attack.





