Risk assessment is the process of identifying, analyzing, and evaluating risk. The only way to verify that the cybersecurity controls you adopt are appropriate to the dangers your business faces is to conduct a risk assessment.
You could lose time, effort, and resources if you don’t use a risk assessment to guide your cybersecurity decisions. After all, there’s no use in putting in place measures to protect against events that are unlikely to happen or won’t have a significant impact on your business. Similarly, you’ll likely underestimate or overlook hazards that could end up costing your company a lot of money.
What does cybersecurity risk assessment contain?
A cybersecurity risk assessment examines the many information assets that could be harmed by a cyber assault (for example, hardware, systems, laptops, customer data, and intellectual property), as well as the numerous threats that could influence those assets.
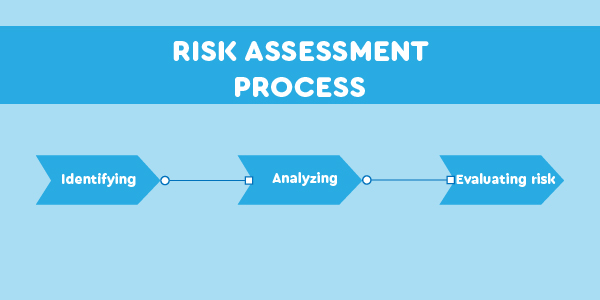
Typically, a risk calculation and evaluation is carried out, followed by the selection of controls to address the risks found. It is critical to continuously monitor and assess the risk environment in order to detect any changes in the organization’s context and to keep track of the entire risk management process.
ISO standards and cyber risks
ISO/IEC 27001:2013 (ISO 27001) is an international standard that specifies the requirements for a best-practice ISMS (information security management system) — a risk-based approach to corporate information security risk management that considers people, processes, and technology.
The norms organisations must follow to comply with ISO must do the following:
- Establish and maintain a set of risk criteria for information security.
- Ensure that risk assessments are “consistent, valid, and comparable” over time.
- Identify “risks connected with the loss of information confidentiality, integrity, and availability within the scope of the information security management system,” as well as the risk owners.
- Analyze and assess information security threats by the previously stated criteria.
- Organizations must “retain documented information on the information security risk assessment process” to verify compliance with these criteria.
As part of the information security risk treatment procedure, they’ll have to undergo several processes and develop required paperwork.





