Dynamic Application Security Testing (DAST) simulates controlled attacks on a web application or service to detect security flaws in a running environment. It evaluates items during operation and provides feedback on compliance and general security issues.
DAST is also referred to as “black-box” tools. These tools are utilized in the SDLC testing and quality assurance phases. The name DAST stems from the test being run in a dynamic environment. Unlike SAST, which searches an application’s code line by line while idle, DAST testing occurs while the application is in use. This isn’t to say that testing doesn’t happen while the program is running. Although DAST can be utilized in production, most testing is done in a quality assurance setting.
How Does DAST Works?
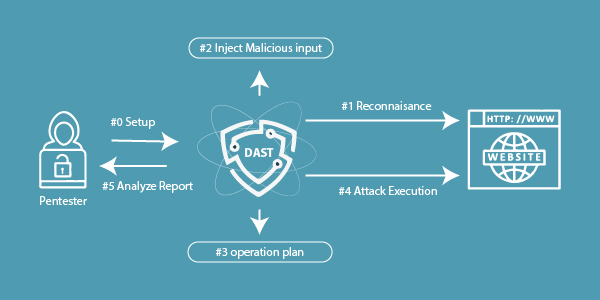
Dynamic Application Security Testing(DAST) runs automated scans on an application to find results that aren’t part of the intended result set. Injecting malicious data to expose typical injection issues is one example. To detect vulnerabilities, DAST tests all HTTP and HTML access points and simulates random activities and user behaviours.
DAST in security testing
Because DAST does not have access to an application’s source code, it detects security flaws by attacking it from the outside. Since DAST does not examine code, it cannot direct testers to specific lines of code when defects are discovered.
When it comes to adopting DAST solutions, security professionals are frequently consulted. Security specialists must often write tests or fine-tune DAST to be helpful. This necessitates a thorough understanding of how the software they’re testing operates and how it’s used. To run DAST efficiently, security experts must have a thorough knowledge of web servers, application servers, databases, access control lists, application traffic flow, and more.
Though they may sound similar, DAST is distinct from penetration testing (also known as pen testing) in critical aspects. DAST provides systematic testing that focuses on the application while it is executing. On the other hand, Pentesting employs conventional hacking techniques with the owner’s consent to exploit vulnerabilities in firewalls, ports, routers, and servers in addition to the application.
Advantages Of Dynamic Application Security Testing

- Focuses on what’s exploitable and covers all components to provide a holistic perspective of application security (server, custom code, open-source, services)
- It can be incorporated into the development, quality assurance, and production to provide a continuous, holistic perspective.
- The dynamic analysis allows for a more comprehensive approach to managing portfolio risk (thousands of apps) and can even scan legacy apps as part of risk management.
- Functional app testing, unlike SAST, is not language bound, allowing for the detection of runtime and environment-related errors.
Disadvantages Of Dynamic Application Security Testing

- It doesn’t assess code or reveal weaknesses in code; instead, it focuses on issues that arise as a result of the code.
- After development is complete, it is used to remedy vulnerabilities, which is more expensive.
- Large projects necessitate technical infrastructure and several instances of the program running simultaneously.
- It generates a lot of false positives.





