Web Application Firewall filters web traffic between the internet and web application. WAF is based on a predefined set of instructions and customized according to the risk and specific needs of the web application. It analyzes the incoming packets and filters out possible threats at the application level.
WHY DO YOU NEED ONE?
With the accelerated rise in the number of companies adopting cloud for running business applications and saving private data, cybercriminals have started to target web applications and websites. A data breach has far-reaching consequences for a business, inducing financial losses and affecting an enterprise’s business and compliance in the short term. Also, a cyber-attack news headline will damage a firm’s reputation, leading to a competitive disadvantage and lost business. This is where Web Application Firewalls (WAF) come into the picture, help enterprises protect internal and public data and applications. WAF helps companies evade costly data breaches and downtime.

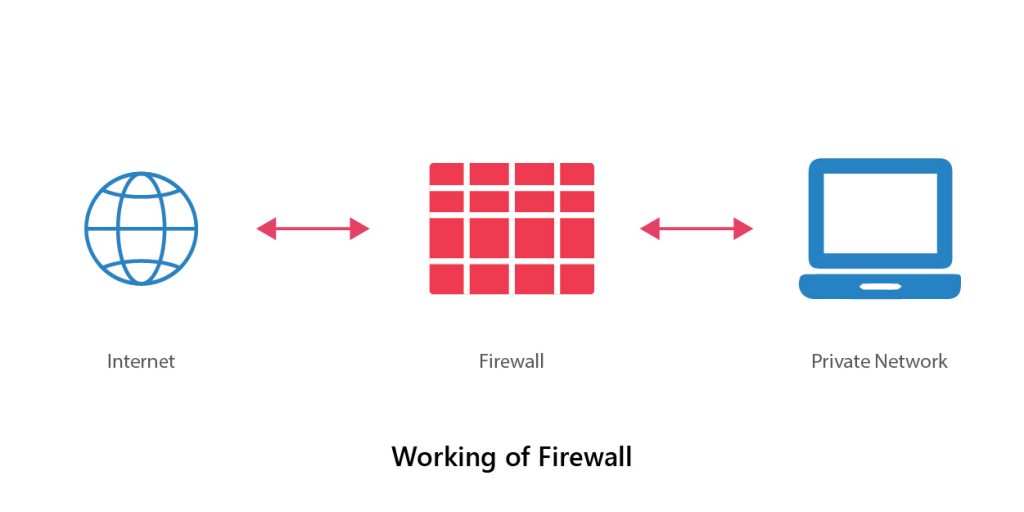
Working of an Enterprise Level Firewall
DIFFERENT TYPES OF WAF MODELS
WAF is categorized into three basic models depending upon the predefined rules or policies.
1. White-list or positive security model
2. Black-list or negative security model
3. Hybrid model
1. Whitelist or positive security model: Positive security model explicitly allows only finite traffic on the system and rejects everything else. Whitelisting prevents the system from being exposed to vulnerabilities that are not anticipated by the developer. It protects the system from “zero-day” attacks by denying access to anonymous traffic. The only disadvantage of this model is it can block requests coming from legitimate resources
2. Blacklist or Negative security model: Negative model grants access to all requests, except for those included in the blacklisted database. The blacklist contains inputs that are anticipated as malicious by the system. This system is easier to implement and can work with any new legitimate sources. The disadvantage is black list has to be constantly updated.
3. Hybrid model: Hybrid is the combination of both the positive and the negative models. It is comprehensively implemented as it contains a set of both a white list and a black list. It is easily customizable to the requirements of the website and offers a high level of security.
ADVANTAGES OF AN ENTERPRISE WAF
Various ways a WAF can benefit a web application include stopping cookie poisoning, preventing SQL injection, obstructing cross-site scripting, and mitigating DOS attacks.
- WAFs protect web applications and APIs against different types of internal and external attacks, such as injection attacks, application-layer denial of service (DoS), cross-site-scripting (XSS), automated attacks (bots), among others. WAFs provide signature-based protection and also help with positive security models and anomaly exposure.
- A WAF is a reverse proxy that protects the server from being exposed by making clients pass through the Web Application Firewall before reaching the server.
- An application firewall works through a set of rules, described as policies. These policies shield the application against vulnerabilities by filtering out malicious traffic.
- A WAF’s value comes in part from the speed and ease with which policy alteration is achieved, allowing a quicker response to different attack vectors. For example, during a DDoS attack, rate limiting can be promptly executed by adjusting WAF policies.





