An injection is a broad class of attack vectors where the attacker provides an altered input to a program. When the input gets executed as a part of a command or a query, the result obtained is completely altered. It is listed as the most dangerous threat in OWASP’s top 10 vulnerabilities.

This flaw allows the malefactors to execute a discrete code on the host operating system through a vulnerable application which could lead to data loss, data corruption, and loss of credibility.
Types of injection
SQL injections are broadly classified into three categories based on their damage potential
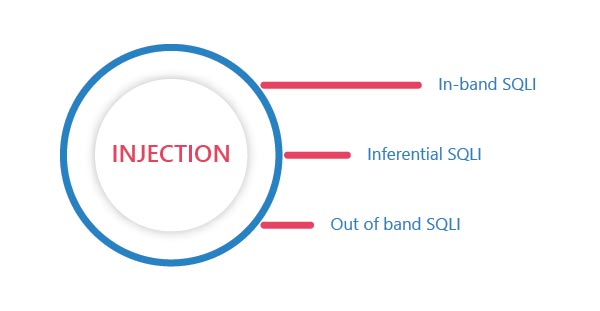
In-Band SQLI: In In-Band SQLI the attacker does the injection when he can make use of the same communication channel as that of the user. It is the most common and easiest out of the SQL Attacks. In-Band SQLI is further classified into two
- Error-based SQL Injection
- Union-based SQL Injection
Error-based SQL Injection: In error-based SQLI the malefactor’s launch attacks are designed to throw error messages towards the database. It helps the attacker in understanding the nature of the database and in some cases it helps them in enumerating the database.
When parameters are manipulated, the server throws SQL Error in detail which was used to successfully explore and exploit the database.
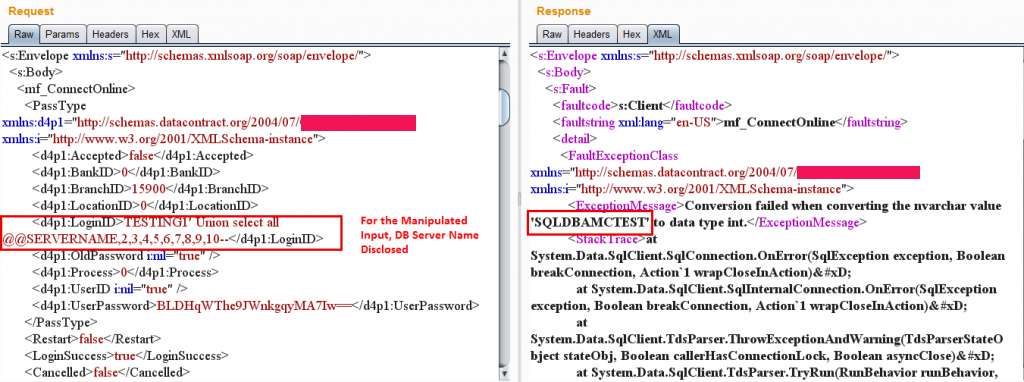
In this case, the error lists a total of 10 Columns of which the first column is vulnerable. With this, the attacker can get the DB server name and its version details
- Database Server name disclosed
- Database name getting disclosed
- Database user name getting disclosed
- Table Name Exposed
- Column Name Exposed
Union-based SQL Injection: Union query SQLI helps the attacker to extract information with the help of a union operator. The attacker gets hold of the information from the database by extending the results from the query. Union operator can be used whenever the original queries have the same number and similar data type of columns.
Inferential SQLI: Inferential SQL injection or blind SQLI communicates with the database and its corresponding HTTP responses do not contain the results of SQL query or traces of any database errors. When the data is not outputted to the web page the hacker questions the database with a series of true or false questions. The main targets for these types of attacks are web applications that show generic error messages instead of generating codes that are vulnerable to the injection. In inferential SQLi no data is transferred between the attacker and the database.
It can be furthermore classified into two types
- Blind Boolean-Based SQL Injection
- Blind Time-sensitive SQL Injection
Blind Boolean-Based SQL Injection: In this type of injection, the attacker tries to understand the nature of the database by sending a set of predefined questions. Based on the results obtained the attacker will determine the vulnerability of the database for the SQL injection.
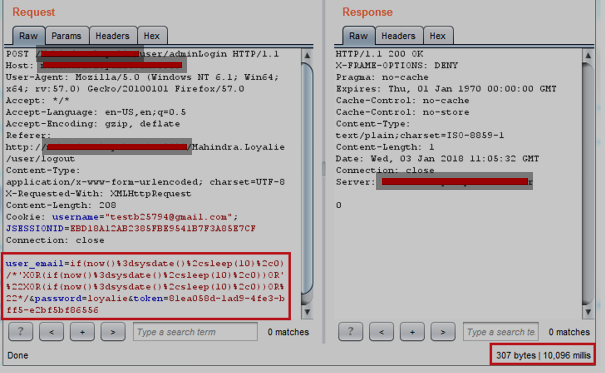
Blind Time-based SQL Injection: Whenever the malefactor interprets the database with a series of true or false questions, the database will wait for a specified amount of time before responding to it. This buffer time is called blind time-based SQLI.
When an asleep time of 10 seconds was given, the application responded after 10 seconds.
Out of Band SQLI: Out of band, SQLI occurs whenever the attacker uses a different channel to attack and obtain results. This type of attack mainly relies on the server’s ability to transmit data over HTTP, SNB, OR DNS protocol. This method is only adopted when attacks based on inferential SQLI or inband SQLI are unstable and inconsistent.
Prevention from SQLI’S: One can prevent the attack of SQLI using sanitized inputs, not connecting the application with the database having root access, identifying the level of permission that the application needs, good code practice may help in preventing the user from SQLI’s
WAF – Web Application Firewall
SQL injection attacks can be prevented with the help of a web application firewall (WAF). A WAF serves as a filter between the server and the web traffic.
A WAF works based on a set of rulesets, the most common type of ruleset used across any WAF is OWASP Top 10 ModSecurity rulesets. StrrongBox IT’s Modshield SB works on the core ModSecurity rulesets, which can avert SQL injections during the time of the attack.





