The Health Insurance Portability Accountability Act was established as federal law by the government of the United States to set the standard for sensitive data protection. Companies dealing with Protected Health Information(PHI) must adopt physical network and process security measures to ensure HIPAA compliance.
Hospitals, doctors, clinics, psychologists, dentists, chiropractors, nursing homes, and pharmacies that handle Protected Health Information (PHI) are considered healthcare providers and need to be HIPAA compliant.
HIPAA has elucidated three rules for protecting the Patient’s Health Information (PHI)
- Privacy rule
- Security rule
- Breach notification rule
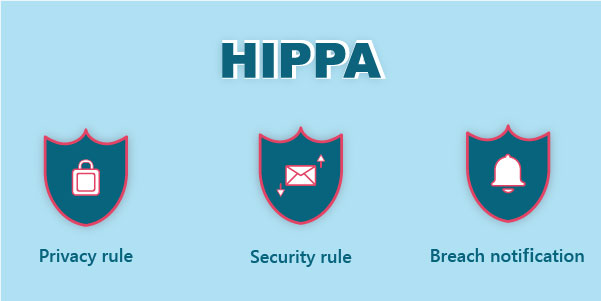
Privacy rule: Privacy Rule assures individuals’ health information is protected. The rule strikes a balance that permits important data use while preserving patients’ privacy. Given that the healthcare marketplace is diverse, the rule is flexible and comprehensive to cover the various services and disclosures that need to be addressed.
Security rule: The Security Rule protects a subset of information covered by the privacy rule, which is all Personally identifiable health information (PIHI), creates, receives, maintains, or transmits in electronic form. The Security Rule applies to health plans, health care clearinghouses, and to any health care provider who transmits health information in electronic form in connection with a transaction for which the Secretary of HHS has adopted standards under HIPAA and business associates.
Breach notification rule: Whenever a network security breach hits an organization, it causes complete chaos in the system. If hackers managed to get in, they’d have access to unlimited patient health data, which they could sell to global entities with bad intentions. This is where HIPAA comes in, it outlines requirements to keep the personal health information of clients and patients safe.
Need Of Data Protection In Health Care Organisations
Healthcare organizations are prime targets for cyber-attacks, given the significance and prevalence of their intellectual property. Unfortunately, the Healthcare industry is lagging behind other industries when it comes to cyber security implementation. With the help of a Web Application Firewall, one can mitigate the consequences ranging from stolen IP, repeating clinical trials, litigation, and lost revenue that resonate throughout an organization.
Additionally, having an enterprise-grade WAF makes your website more secure and enhances the web application’s performance.
StrongBox IT is a cybersecurity provider offering an enterprise-grade Web Application Firewall (WAF) – Modshield SB. Modshield SB is built with ModSecurity CRS and 2021 OWASP Standards.
MODSHIELD SB WAF defends against a wide range of web-based instructions and attacks that target applications hosted on the cloud and web applications. Modshield SB scans both inbound and outbound traffic, thereby protecting the user from attacks and preventing data loss (DLP). In addition, MODSHIELD SB protects from cross-site scripting (XSS), Server-side request forgery (SSRF), Sensitive data exposure, and other malicious attacks by hackers that compromise the privacy and integrity of sensitive data. By installing Modshield SB on the server, one can protect their web applications and satisfy HIPAA compliance control in one step.





